Phishing Defense: Catching Digital Doppelgängers When It’s Your Brand on the Line
KELA is putting defensive strategies in the spotlight, and looking at how enterprises can ward off the growing threat of phishing attacks that mimic their brand.
Updated April 10, 2025.

Ping! An email arrives in your customer or partner’s inbox. They see your company name, their own details at the top, right by the familiar logo and branding. An offer, a reward, a request… the reader doesn’t think twice. Why would they? They’ve known you and your company for years - and they trust you.
Click. They’re taken to a landing page that looks just like your own.
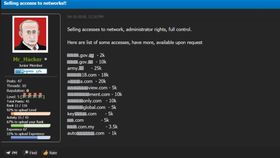
That’s all it takes for an attacker to complete a successful phishing scam when they are using your organization as bait. And as we discussed last time, in part one of our Phishing-as-a-Service (PhaaS) series, it’s now easier than ever to grab everything needed to launch and scale this kind of attack, thanks to the growth of a subscription-based economy that commodotizes access to targeted phishing templates, credential harvesting tools, and even customer support.
In the second part of this series, KELA is putting defensive strategies in the spotlight, and looking at how enterprises can ward off the growing threat of phishing attacks that mimic their brand.
Why Should Enterprises Care About Phishing Scams that Impersonate their Company?
When most people think about the risk of phishing scams, their first thought is an attack that arrives through their own employees’ inboxes. When an employee inadvertently clicks on a phishing link or downloads a malicious attachment, they are opening the business up to credential harvesting, ransomware or data breaches. Most companies have proactive protections in place such as email security and filtering solutions and ongoing employee awareness and training programs to help employees spot malicious emails. Multi-factor Authentication can also reduce the likelihood of credentials being used, even if employees do fall victim to a scam.
But what about when you land on the other side of a phishing scam, when attackers have leveraged your good name as a weapon to attack other companies? If this wasn’t already on your radar, it should be. These attacks happen entirely outside of your own network, and can cause:
Brand damage: When attackers impersonate your brand in a phishing email, your customers, your partners, and your employees can all fall victim to scams. As soon as your customer or supply chain partners associate your company with fraudulent activities, you can wave goodbye to renewals, referrals, and trust.
Leaked information: When attacks mimic your brand, they can trick users into handing over sensitive information including their login credentials, their payment details, or their personal data. Attackers can then use this information to cause deeper harm, or in the case of employee info, they can launch a further attack against your network.
Financial losses: When a phishing attack is successful, it can lead to identity theft, Business Email Compromise (BEC), or other cases of financial fraud. This can cause millions in direct losses, added to the bill for remediation and legal support in taking down false assets or fighting regulatory action.
Compliance failures: Regulations such as GDPR, CCPA and more all impose strict data protection rules, and can hold a company liable if they feel the business has failed to protect their customers from brand attacks.
One of the worst parts about a brand impersonation attack is that your customers or your partners usually know about it before you do. As the attack takes place completely outside of your network, you may find yourself totally in the dark. The first you might hear of it is an angry customer who has suffered a data breach, legal or class action activity against your brand. Or in the case of an attack against your own employees, the next stage of the threat against your own network.
KELA Brand Control: Defending Against Brand Attacks
In 2023, organizations faced an estimated $17,700 loss per minute due to phishing-related cyberattacks. KELA Brand Control aims to reduce that risk with real-time monitoring, early threat detection, and rapid takedown capabilities to neutralize cyber threats before they cause damage. Leveraging KELA’s vast proprietary dataset and advanced AI-driven analytics, Brand Control delivers comprehensive protection across web domains and social media.
Security teams can benefit from the broad and comprehensive coverage. Data shows that Brand Control can dramatically reduce successful phishing attempts by 75-85%, and it ensures brands can maintain customer trust and integrity.
Brand Control works by scanning for abuse in both public and proprietary sources across the open, deep and dark web — looking for suspicious websites that target and misuse your brand. It detects lookalike domains and subdomains, uncovers typosquatting attacks and highlights any websites that are impersonating your brand assets such as your logos, imagery or themes. Brand Control even monitors social media accounts, to ensure there are no pages or users impersonating your employees.
Incidents are automatically classified and prioritized for rapid remediation, with a fully automated system that blocks phishing sites in minutes, and takes them down within just a few hours.
The emergence and growth of PhaSS have made phishing attacks more prevalent than ever, and blind spots are an attacker’s best friend. Learn more about how Brand Control can help you eliminate phishing threats faster than ever before.