How Phishing-as-a-Service Fuels Cybercrime at Scale
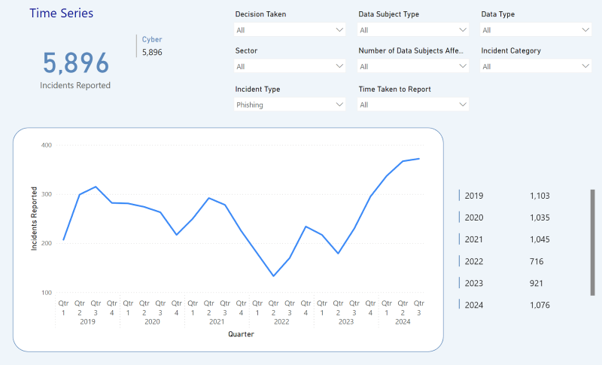
More cyber incidents were caused by phishing in Q3 2024 than any time in the past five years, according to the most recent data from the ICO. While we would all like to think we’ve gotten more savvy at ignoring all those iPads we keep “winning” — there’s a threat actor tactic that’s making it easier than ever for criminals to launch successful phishing campaigns.
Updated April 3, 2025.

More cyber incidents were caused by phishing in Q3 2024 than any time in the past five years, according to the most recent data from the ICO. While we would all like to think we’ve gotten more savvy at ignoring all those iPads we keep “winning” — there’s a threat actor tactic that’s making it easier than ever for criminals to launch successful phishing campaigns.
One of the contributors to the rise in phishing attacks is the growth in Phishing-as-a-Service (PhaaS), where cybercriminals now have access to ready-made phishing tools, infrastructure, and support to conduct attacks without the need for technical expertise. This two-part series will look at the growth of PhaaS, how it works in the wild, and defensive strategies that you can use to stay two steps ahead from tomorrow’s phishing attack-related headline.
What is Phishing-as-a-Service (PhaaS)?
We’re pretty sure that about four seconds after Ray Tomlinson sent the first ever email in the 1970s, he was receiving special time-sensitive offers in return for login credentials and financial data. In short? Phishing has been around for almost as long as the internet itself. But back in the day, to launch a phishing attack, bad actors needed more technical prowess. Individuals would have to craft compelling emails, build systems for credential harvesting, and come up with ways to keep themselves hidden to evade detection. The perfect crime for the nefarious and tech-savvy introvert.
One shift has been the move from attacks that target individuals to phishing scams that put businesses squarely in their viewfinder. KELA reports indicate a growing trend of business-targeted phishing campaigns, specifically against executives and IT admins. Attackers use PhaaS services to bypass Multi-Factor Authentication and to infiltrate corporate networks, often leading to data breaches and ransomware attacks.
Another evolution to watch is phishing taking the shift from a DIY activity to a fully-fledged subscription-based economy, and there are now dozens of PhaaS platforms where cybercriminals can purchase anything from targeted phishing templates to hosting services. Attackers can use the PhaaS model to access pre-built templates for a specific industry or attack vector, like a banking template for a mobile app phishing attack on a high-value finance target, or an SMS phishing scam aimed at a specific healthcare organization. They can add on automated tools for credential harvesting, anti-detection and evasion techniques, and even customer support if they need a bit of hand holding being dastardly.
Geographic spotlight: KELA research has highlighted a recent increase in PhaaS that targets Japan, with Chinese-speaking cybercriminals leading the charge. Unlike services that focus on Western targets, these groups custom-build phishing kits which are tailored to Japanese financial institutions for example, showing the growing global issue that PhaaS presents.
Which PhaaS Platforms Should I Be Aware of?
Let’s dive a bit deeper into some PhaaS platforms that are lowering the barrier to entry for cybercriminals:
Tycoon 2FA: Tycoon is an advanced phishing kit that enables attackers to bypass multi-factor authentication (MFA) by intercepting user credentials and session cookies. It incorporates sophisticated evasion techniques, such as blocking developer tools and obfuscating code, making detection and analysis challenging.
Rockstar 2FA: Designed to steal Microsoft 365 credentials, and operated by a threat actor tracked by Microsoft as Storm-1575, this Phishing-as-a-Service toolkit is also capable of bypassing MFA protections. It offers customizable phishing themes and integrates with Telegram bots, allowing attackers to manage campaigns with minimal technical expertise.
Robin Banks: Targeting the financial sector, Robin Banks offers ready-made phishing kits impersonating major institutions globally including Citibank, Bank of America, Capital One, Wells Fargo, and Lloyds Bank. It offers customizable templates and real-time dashboards, enabling even inexperienced cybercriminals to launch effective phishing campaigns.
Astaroth: This phishing kit has been linked with attacks targeting Gmail and Outlook users. Cybercriminals utilizing Astaroth have managed to intercept login credentials and bypass two-factor authentication by capturing session cookies. Victims have reported unauthorized access to their email accounts, leading to potential data breaches and financial losses.
EvilProxy: a (PhaaS) platform that enables cybercriminals to bypass multi-factor authentication (MFA) using a reverse proxy technique. First advertised in July 2022 and still active today, KELA's research suggests that it evolved from earlier phishing tools dating back to 2020. EvilProxy provides subscription-based access to a platform where attackers can easily launch phishing campaigns targeting services like Google, Microsoft, LinkedIn, and Facebook, capturing credentials and session cookies.
The Cybercrime Market: Who’s Buying and Selling?
Phishing-as-a-Service has grown as a result of organized cybercriminal groups, nation-state actors and profit-driven hackers, all of whom recognize the value of selling their expertise or organizational skills through a structured or subscription-based model. On the other side of the transaction, some attackers leverage PhaaS because they aren’t A+ students, and just don’t have the skills to manage a phishing attack end-to-end. Others are advanced threat actors who just want to save time. For some, the real focus is getting in on a ransomware attack for example, and as affiliates they want the easiest route possible to getting those credentials and obtaining initial access.
How is it all going down? We’re glad you asked. In terms of where it’s happening, these buyers and sellers often use Telegram as their primary communication and sales channel. This means they can leverage features like encrypted messaging and ease of access to distribute and buy phishing tools and services. Operators might have their own exclusive or invite-only Telegram groups where they can post advertisements, share updates (“New phishing template live now”), or provide customer support or helpdesk functionality for criminals who subscribe on a monthly basis. Here, experts will answer questions to support attackers with deploying phishing kits, setting up domains, or bypassing specific security measures.
Looking at finances, PhaaS providers will usually want upfront payments for their phishing kits, or enforce a subscription-based model where monthly fees are charged for access to templates, hosting and credential theft services. To pay the piper, most transactions will be conducted using cryptocurrency, making payments much harder to trace.
In some cases, operators of PhaaS platforms will offer more sophisticated features. Think about dashboards that allow phishing campaign management such as monitoring victims or tracking stolen credentials. KELA research reveals that some PhaaS providers are now expanding their offerings beyond phishing, integrating hybrid cybercrime techniques such as infostealers, keyloggers and ransomware to scale operations past the initial phishing scam into offering a full cybercrime toolkit. In this way, attackers can automatically exploit compromised credentials for account takeovers, fraud, or data exfiltration, all from a single platform.
The Future of PhaaS: What’s Next?
Unfortunately, things aren’t likely to get better any time soon.
Forbes warns of “Uncensored AI chatbots [which] operate without guardrails, raising serious concerns about potential misuse.” Examples like GhostGPT eliminate the ethical and security restrictions we typically expect to be built into LLMs, and are therefore perfect for writing convincing phishing emails or campaigns. In addition, deepfakes have made phishing harder to spot — such as one example where fraudsters used AI to mimic a CEO’s voice, instructing an employee to complete a transaction worth almost $250,000.
While law enforcement is attempting to crack down on PhaaS, such as the recent takedown of LabHost or the FBI’s action against a group it calls Saim Raza, it’s impossible to fully stem the wave of attacks that Phishing-as-a-Service has created. In this reality, proactive cybersecurity measures are crucial.
Keep an eye out for part two of this series, where we embrace the positive, and cover what defenses can be used against the growing risk exacerbated by Phishing-as-a-Service.
In the meantime, if you’re eager to start thinking about protection, check out our new Brand Control solution that launched this week.