Hellcat Hacking Group Unmasked: Investigating Rey and Pryx
KELA reveals the real identities behind Rey and Pryx, the key players driving Hellcat’s cybercrime operations. From high-profile data breaches to controversial online activities, our investigation uncovers OSINT traces, leaked credentials, and hidden connections.
Published March 27, 2025.

Hellcat, a notorious hacking group that burst onto the cybercrime scene in late 2024, has been making waves with its high-profile attacks on major corporations like Schneider Electric, Telefónica, and Orange Romania. Originally known as "ICA Group," Hellcat quickly cemented its reputation as a major threat. At the heart of this operation are two key threat actors: Pryx and Rey. New findings, evident from their activities across different cybercrime forums, social media and other online platforms, disclose their real identities. KELA’s latest research uncovers key insights into Pryx, Rey, and their tactics—empowering law enforcement and helping organizations avoid becoming the next target.
While KELA has already disclosed the findings to some key law enforcement and federal agencies in regions including the United States, Europe and APAC, the full threat actor profiles for both individuals, including exclusive and full details not covered in this blog. They are available to KELA customers and upon request here.
Who is Rey/Hikki-Chan?
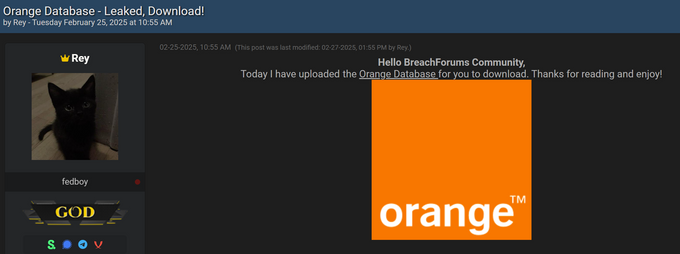
Rey, previously known as "Hikki-Chan”, surfaced on BreachForums in early 2024, quickly attracting attention with data leaks and claims of high-profile breaches. However, many of his supposed exclusive leaks, such as VK and Kavim, were later exposed as repackaged older breaches, undermining his credibility. Despite this, he rebranded as “Rey” in late 2024 and remained active in cybercrime, becoming the administrator of the Hellcat group. His operations frequently involved exploiting Jira credentials to gain access to sensitive data in multiple companies, including recently claimed attacks on Jaguar and Ascom. While he also joined the XSS forum in November 2024, his presence there was minimal.
Rey maintains an aggressive and controversial online presence, using platforms like Telegram and X to share leaks, criticize telecom security, and make inflammatory statements. His messages frequently reference hacking techniques, cryptocurrency scams, and cybercriminal tools while also containing hate speech and toxic rhetoric. Rey identified himself as a cryptography expert who began hacking in 2020, initially focusing on website defacements. He claims to avoid targeting healthcare organizations. Rey expresses a cynical view of the hacker community, portraying himself as a calculated and pragmatic cybercriminal.
OSINT Traces
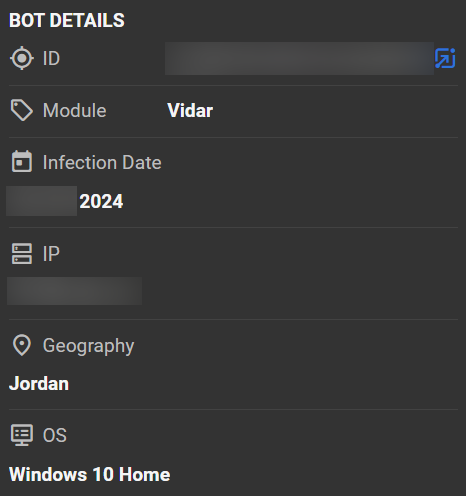
KELA's data lake revealed that Rey was infected by an infostealer on two separate occasions, in February (Redline stealer) and March 2024 (Vidar stealer), when he used the Hikki-Chan moniker. One of the infected bots was likely operating on a shared computer used by a family member. The bot was traced back to a young individual named “Saif” (full name redacted by KELA in this blog) from Amman, Jordan, uncovering possibly Rey’s identity and origins.
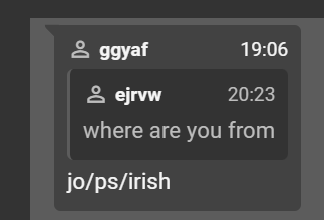
Further investigation into the infostealer uncovered Rey’s previous online aliases and activities. Before adopting the username “Hikki-Chan”, he primarily used "ggyaf" and “o5tdev” on hacking forums such as RaidForums, BreachForums, and other cybercrime communities. He also maintained various accounts on platforms like GitHub, ProtonMail, and cock.li. Under the moniker “o5tdev”, he focused on hacking websites and defacing them, as he mentioned in his interview. In a Pastebin post, he described himself as a “Palestinian hacker” and declared, “I’m not afraid of anything, just Allah”, being part of Anonymous Palestine. In one of his old monikers, Rey mentioned he was of Palestinian and Jordanian origin, which was also linked to Ireland.
Who is Pryx/HolyPryx?
Pryx is a cybercriminal active since around June 2024 across multiple platforms including XSS, BreachForums, Dread, Telegram, and X (Twitter), and engages deeply in technical discussions and competitions. Before joining Hellcat, he started with solo data leaks from educational institutions before escalating to government systems in UAE, Saudi Arabia, and Barbados. He later expanded to targeting private companies, while also selling malware such as AES256-based crypter. He also maintained a personal blog (pryx.pw, formerly pryx.cc).
KELA was able to detect some Telegram groups where the actor was active, showing he is an Arabic speaker. According to him, he has been involved in carding since 2018. Pryx has made controversial and offensive statements including racist and anti-Semitic remarks, and has issued threats, including a bomb threat against Harvard University on his X profile. As of February 2025, Pryx shifted his focus from Telegram to the X platform.
The actor actively promoted the now-defunct DangerZone cybercrime forum but denied any ownership, attributing it to "Sileo," whom the user suspects to be the threat actor “Astounding”, the former administrator of BlackForums. Pryx also claimed to develop a “unique server-side stealer", which uses Tor-based services on victims' systems to exfiltrate data. Unlike traditional stealers, it establishes a hidden access point on the victim's device, enabling data harvesting to occur remotely on the attacker's server. This reduces detection risks and minimizes network traces by limiting outbound data exfiltration.
OSINT Traces
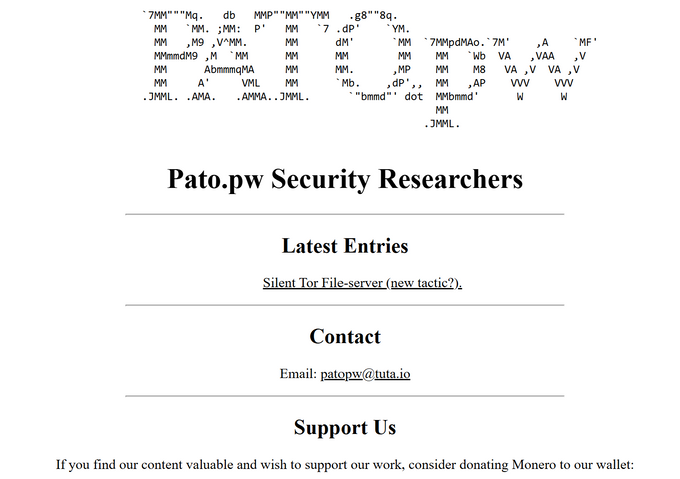
Technical analysis of one of Pryx’s malware source code reveals evidence linking Pryx to the domain pato.pw. The pato.pw website presented itself as a platform for security researchers, offering contact information, cryptocurrency donation options, and an onion address, but KELA’s findings indicate it was primarily operated by Pryx. A significant finding was a July 23 guide titled "Silent Tor File-server (new tactic?)" which described a server-side stealer matching Pryx's stealer, featuring screenshots identical to those in a YouTube video Pryx created for an XSS competition. This content appeared on pato.pw two weeks before Pryx shared it on the XSS forum.
Further investigation revealed a GitHub repository linked to pato.pw. Although the repository owner changed their username from "patopw" to another name in an apparent attempt to hide the connection, the associated email from the website remained the same. Additionally, a file in the repository had an identical hash to one Pryx had shared on Telegram. An archived version of the guide in the pato.pw website from June 30, 2024, listed an author named "Adem" (full name redacted by KELA), though this detail was later removed. Using this name, KELA linked the activity to an individual in the UAE, who originates from a different Arab country, and identifies as a cybersecurity expert. Using the individual’s contact details, KELA found a related infostealer bot originating from the UAE in our data lake.
Data from the infostealer bot linked the individual to the threat actor Weed/WeedSec. An X profile that was found related, referenced “weedforums.lol”, which led to a Telegram user named “weedforums”, found in KELA’s data. Their chat activity revealed a close friendship with Astounding, the suspected admin of DangerZone and BlackForums, further suggesting that Pryx and Weed/WeedSec are likely the same person. Additionally, further analysis uncovered that this Telegram user had also used the alias “Adem”, as mentioned earlier, which points to a possible circumstantial association with the Pryx’s identity.
Bottom Line
In conclusion, the Hellcat hacking group, led by key actors Rey and Pryx, has rapidly gained notoriety in the cybercrime landscape. Rey, previously known as Hikki-Chan, has been involved in high-profile breaches and data leaks, while Pryx has escalated from solo attacks to targeting government systems and private companies. Both individuals maintain a controversial online presence, using various platforms to further their malicious activities. KELA's research has uncovered critical OSINT traces, providing compelling evidence connecting Rey and Pryx to specific online personas and potential real-world identities through infostealer infections and technical analysis. Ironically, Rey and Pryx, who heavily relied on infostealer logs in their operations, fell victim to it themselves.
If any government or law enforcement agency seeks more information, please reach out to KELA.